Information Security Management
From Accountable to Qualified
Become a Designated Qualified Individual
Event Starts In…
Being an Information Security Manager isn’t about fixing computers.
It’s about stewarding organizational risk, protecting sensitive data,
and ensuring compliance with laws that carry real penalties.
This role now carries personal accountability, expectations of competence,
and—yes—potential liability if things go wrong.
Regulated industries require more than scattered documents.
They require a formalized, auditable system of governance:
- Written policies
- Documented procedures
- Risk assessments
- Incident response
- Testing
- Training
- Vendor oversight
- Program review
Technical controls matter, but regulators judge your program, not your tools.
A qualified manager understands:
- How risk ties into decisions
- Which safeguards satisfy regulatory expectations
- How to demonstrate due diligence
- How to prove the organization made “reasonable security decisions”
Regulatory bodies don’t ask, “Did you mean well?”
They ask:
- Show me the evidence.
- Show me the decision trail.
- Show me how you evaluated risk.
You cannot—and should not—do everything yourself.
Being qualified means learning to:
- Drive accountability across departments
- Facilitate compliance, not shoulder it
- Engage leadership in decision-making
- Build a culture that supports security
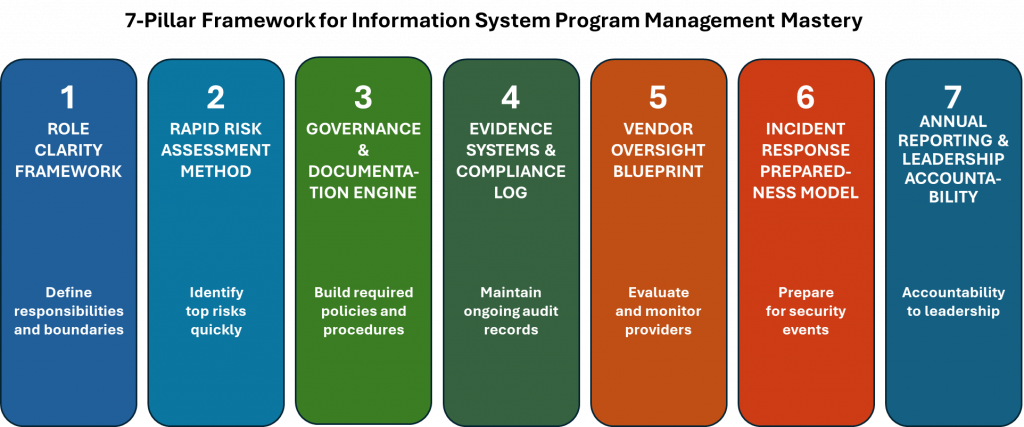
You become qualified by learning a repeatable, proven process for building and managing a security program that meets regulatory standards.
- What regulators expect
- How to implement those expectations
- How to document them
- How to manage them year-round
Typical Security Manager vs. DQI-Trained Security Manager A Clear Contrast in Capability, Clarity, and Accountability
Category | Typical Security Manager | DQI-Trained Security Manager (DQI Academy) |
Role Clarity | Often unclear about full scope of responsibilities; responsibilities are informally assigned and loosely defined. | Has explicit role boundaries, expectations, and accountability aligned with GLBA, HIPAA, FTC Safeguards, and regulatory intent. |
Program Structure | Works within fragmented, inherited, or outdated documentation and processes. | Operates a unified, 7-Pillar Security Program Management Framework with repeatable workflows and evidence paths. |
Regulatory Alignment | Reactive—reviews requirements when audits or incidents force it. | Proactive—maps operations to regulatory controls, builds defensible documentation, and demonstrates ongoing due diligence. |
Risk Management | Performs risk assessments irregularly, often using templates not tied to decision-making. | Drives continuous, rapid-risk cycles using standardized, evidence-based methods purpose-built for small/regulated environments. |
Technical Overwhelm | Frequently feels buried in alerts, tasks, tools, and competing expectations. | Uses structured prioritization and operational clarity to eliminate noise and focus on business-relevant risks. |
Leadership Confidence | Hesitates to make decisions due to fear of blame or misunderstanding regulatory expectations. | Acts with confidence grounded in a defensible process, documented reasoning, and clear authority. |
Communication With Executives | Speaks in technical terms; struggles to get buy-in or funding. | Communicates in business language—risk, liability, operational impact, financial exposure. Gets decisions made. |
Incident Readiness | Depends heavily on IT or vendors; lacks clear, documented procedures unique to their organization. | Executes a structured incident management playbook tied to regulatory expectations, evidence requirements, and leadership communication. |
Liability Awareness | Often unaware of personal accountability for failures in oversight, documentation, or reporting. | Fully understands personal regulatory exposure and operates a defensible governance process to minimize organizational and personal risk. |
Documentation Quality | Scattered documents, missing artifacts, inconsistent updates. | Precise, version-controlled documentation aligned to a governance timeline and audit-ready at all times. |
Vendor Oversight | Relies on trust or minimal questionnaires; rarely performs true due diligence. | Performs systematic vendor risk reviews with clear criteria, documentation, and follow-through actions. |
Audit Preparedness | Scrambles before audits; struggles to produce evidence that matches requirements. | Always ready—controls are mapped, evidence is collected continuously, and the narrative is clear and defensible. |
Decision-Making Process | Decisions feel subjective, rushed, or politically influenced. | Uses a structured, repeatable decision framework that stands up to scrutiny from regulators, auditors, and legal counsel. |
Time Management | Constant firefighting; unclear priorities; reactive mode dominates. | Operates from a predictable weekly cadence using the DQI Confidence System, reducing chaos and burnout. |
Career Trajectory | Often plateaus due to lack of strategic credibility or uncertainty in execution. | Becomes a trusted advisor to leadership, positioned for advancement to Director, vCISO, or full CISO roles. |
